engineering & technology publications
ISSN 1759-3433
PROCEEDINGS OF THE FIFTH INTERNATIONAL CONFERENCE ON ENGINEERING COMPUTATIONAL TECHNOLOGY
Symmetric Block Ciphers Based on Cellular Automata
1Department of Applied Mathematics, Universidad de Salamanca, Spain
2Department of Information Processing and Coding, C.S.I.C., Spain
Let I be a colored image defined by
![]() pixels and a palette of c colors. Then, the image I can be
represented as a linear array of n elements, M, with
coefficients in
pixels and a palette of c colors. Then, the image I can be
represented as a linear array of n elements, M, with
coefficients in
![]() , where
, where ![]() , and
, and
![]() , for black & white, grey-level and colored
images, respectively.
, for black & white, grey-level and colored
images, respectively.
The proposed cryptosystem consists of three phases. In the first phase, the setup phase, the two users agree the key to be shared and the cellular automaton (CA) to be used is defined. In the second phase, the encryption phase, the sender chooses a truly random generator or a CSPRBG and encrypts the secret image to be sent to the receiver. Finally, in the third phase, the decryption phase, the receiver uses the inverse CA to the one considered in the setup phase and decrypts the received image.
Specifically, the protocol is as follows:
Before encrypting an image, the sender and the receiver, Alice and Bob, respectively, agree to use a 128-bit secret key for the cryptosystem:
The one-dimensional reversible memory cellular automaton proposed to be
used in the cryptosystem for encrypting is
![]() , and its inverse CA,
, and its inverse CA,
![]() , is used for decrypting, where:
, is used for decrypting, where:
- The cellular space,
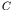 , is a linear array of size
, is a linear array of size 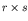 .
.
- The state set is given by
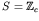 .
.
- The set of indices
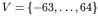 is selected so
that each cell
is selected so
that each cell
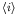 has the following neighborhood
has the following neighborhood
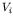 :
:
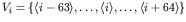 .
.
- The transition function of
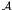 , f, is defined as follows
where
, f, is defined as follows
where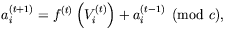
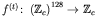 is defined from the 128 bits secret key, K as follows:
and where
is defined from the 128 bits secret key, K as follows:
and where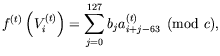
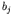 ,
,
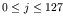 , are the bits of the key K
given in the expression (66).
Hence, the new state of the cell
, are the bits of the key K
given in the expression (66).
Hence, the new state of the cell
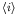 at time t+1
is determined by the following expression
at time t+1
is determined by the following expression
Note that the transition function of
![]() , f, permits
to define its CA inverse by defining the transition function
, f, permits
to define its CA inverse by defining the transition function
![]() of
of
![]() by the expression
by the expression
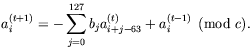
For encrypting a black & white, grey-level or colored image, I,
Alice considers its representation as a linear array, M, of
![]() coefficients in
coefficients in
![]() . Moreover, she chooses
either a truly random or a CSPRBG and develops the following
protocol:
. Moreover, she chooses
either a truly random or a CSPRBG and develops the following
protocol:
- Alice considers the linear array M as the initial
configuration of
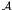 :
:
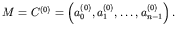
- Alice uses the CSPRBG in order to obtain a sequence
of n integers in
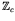 :
:
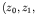
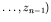 , for each image. This set can be considered as the
configuration
, for each image. This set can be considered as the
configuration
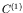 of the cellular automaton
of the cellular automaton
 , by taking
, by taking
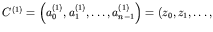
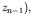 that is,
that is,
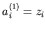 ,
,
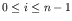 . Once
the protocol has finished, this configuration,
. Once
the protocol has finished, this configuration, 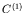 ,can be
destroyed.
,can be
destroyed.
- Alice encrypts each pixel of I, that is, determines the new
states of each cell of the configuration
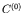 by means of
determining two evolutions of the cellular automaton
by means of
determining two evolutions of the cellular automaton
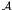 ,
, 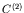 and
and 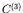 , by using the formula
(67). In this way, Alice obtains the encrypted array
of M,
, by using the formula
(67). In this way, Alice obtains the encrypted array
of M, 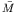 , which is formed by the concatenation of the two
evolutions computed:
, which is formed by the concatenation of the two
evolutions computed:
purchase the full-text of this paper (price £20)
go to the previous paper
go to the next paper
return to the table of contents
return to the book description
purchase this book (price £105 +P&P)